see this link https://electrondust.com/2017/11/25/setting-raspberry-pi-wifi-static-ip-raspbian-stretch-lite/
Cool GPX Flyover
This site is very cool. http://gpxhyperlapse.com/ just drag over your .gpx file and you get a google flyover of the route.
Getting a Raspberry Pi to operate an old Bye Bye Standby (BBSB) RF 433 switch
Introduction
I decided to go and re-visit an old project. Getting my Raspberry Pi to switch some old RF plugs. I tried earlier this year or maybe last year and could never work it out.
This was prompted by a random google to this site. https://www.instructables.com/id/Control-RF-Outlets-With-Raspberry-Pi-3-433mHz-Rece/ and as I had all the “bits” I thought I would try again.
Installing Hassbian on the Pi
Things are never simple. Firstly getting a version of Hassbian onto the memory card seems to be much harder than I expected. The link in the article above was not to the latest version (Why would it be?) and looking further I found the install instructions here. https://www.home-assistant.io/docs/installation/hassbian/installation/. Once I had booted the Pi it seems that Hassbian was not corrected loaded so I upgraded in installation using “sudo hassbian-config upgrade hassbian”. This took a while to run (30+ mins). Then followed instructions and added
- Samba
sudo apt-get update
sudo apt-get upgrade
sudo hassbian-config install samba - WiringPi
sudo git clone git://git.drogon.net/wiringPi
cd wiring Pi
sudo ./build - Check using
gpio -v - Install RFSniffer
sudo git clone git://github.com/timleland/rfoutlet.git /var/www/rfoutlet
sudo chown root.root /var/www/rfoutlet/codesend
sudo chmod 4755 /var/www/rfoutlet/codesend
Pi Hardware – Receiver and Transmitter
Lets have a look at the hardware. I have a breakout board from the Pi which helps.
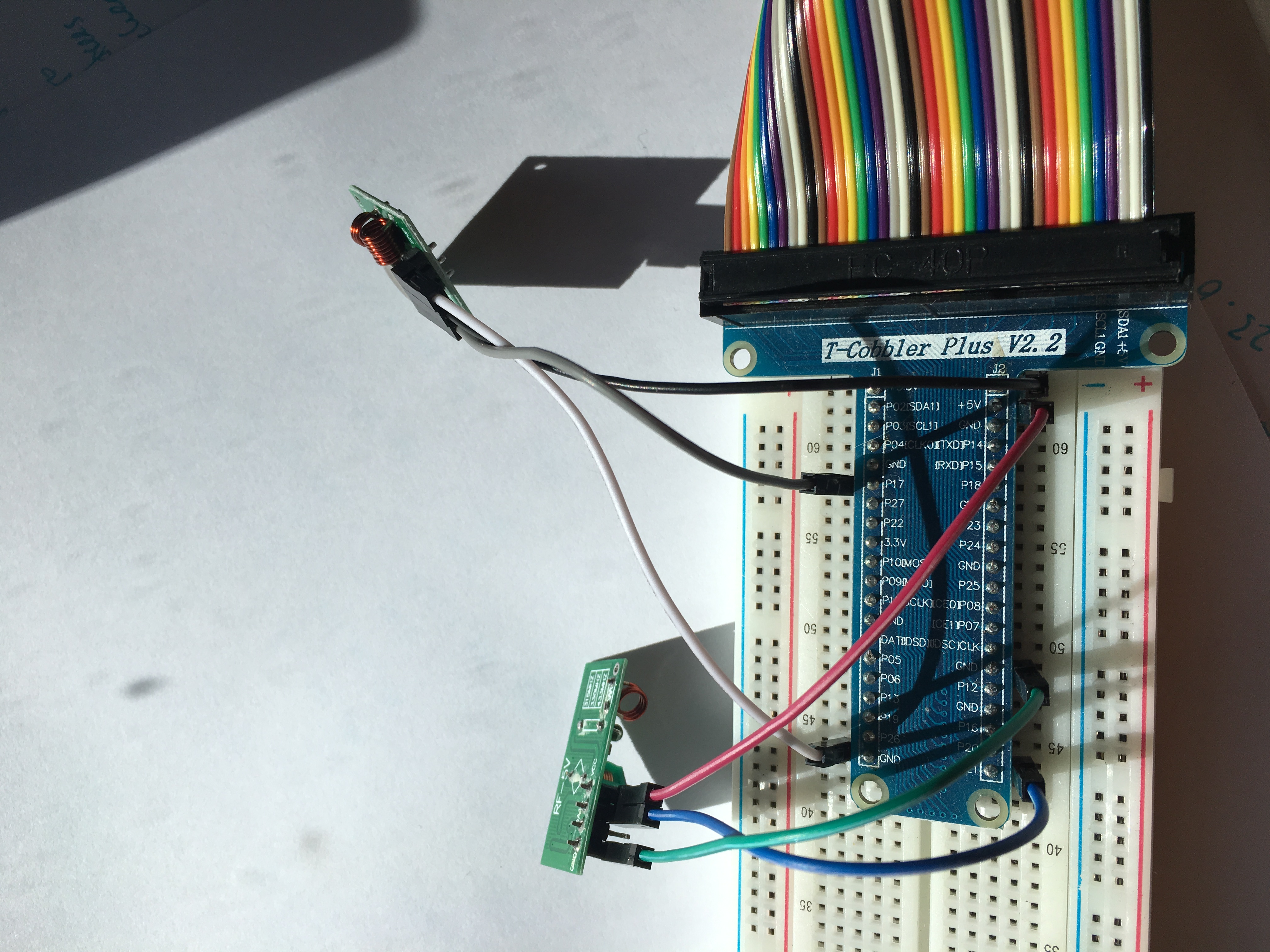


The hardware is wired like this
Receiver
– VCC – 5v (Black wire)
– GND – GND bottom left (white wire)
– DATA – P17 (grey wire)
Transmitter
– VCC – 5v (Red wire)
– GND – GND middle (green wire)
– DATA – P21 (blue wire)
Now all wired up and software running.
Nothing works…. yet…. the investigation
Time to run RFSniffer
sudo /var/www/rfoutlet/RFSniffer
and as expected there is a blank screen. However clicking the BBSB remote seems to detect nothing even though the switch is turning on and off.
Well it seems I have not got what I want! I wondered if the GPIO was receiving anything. I found out I could install piscope and send the output to an X11 server. http://abyz.me.uk/rpi/pigpio/piscope.html. Some more installing of software Xming for the PC and pigpiod etc and I could then run piscope &. What I discovered was a Channel 21 was indeed receiving data but masses of noise so anything I might have been sending looked like it was lost in a sea and so RFSniffer was not getting anything different.
Some more googling and went here http://abyz.me.uk/rpi/pigpio/examples.html#pdif2__433D. Downloaded the 433Mhz Keyfob RX/TX software.
Getting this running indicated that the receiver was indeed getting data but that the format of the data was not Manchester encoding which is what this software is meant to do.
Getting the Bye Bye Standbye switches working
How do I find out what encoding does the BBSB use? Google again! It seems that BBSB is simple I found references to Home Easy Simple protocols. I tried using Pilight but could not work out how to configure it easily so tried looking further. Then found reference to KAKU OOK protocol. I eventually landed up installing rfctl from here https://github.com/troglobit/rfctl. The instructions are not for a newbie like me the command
sudo apt install raspberry-kernel-headers
was OK but then when I looked in /lib/modules there seems to be 2 directories. Which one? I eventually used 14.14.70+ and not 14.14.70-v7+. Took me a while to work out that I needed to do the following
cd /lib/modules/14.14.70+
sudo git clone https://github.com/troglobit/rfctl.git
but once past that simple bit the instructions are clear (but I needed to run as sudo)
cd rfctl/kernel
sudo make
sudo make install
cd rfctl/src
sudo make
cd make install
I have my BBSB set to A3 so trying the following worked a treat
this turns on
rfctl -p NEXA -g A -c 3 -l 1
and this turns off
rfctl -p NEXA -g A -c 3 -l 0
Now how to integrate this into Home Assistant.
When I Googled the remote model number WST-8500 and found the receiver model numbers are YCR-300,YCR-3500,WSR-1000,LCMR-1000,LCMR-300. Not sure if this is going to help in the future or not.
Integrating into a single command
The next step is to be able to run this command remotely from the main Home Assistant server as I will not be using the HA on the Pi and will stop Hass from running at boot time.
So for passwordless ssh from the HA server to the Pi I created some ssh keys using command
ssh-keygen
on the HA server while logged in as the homeassistant user. (it turns out that HA is running under root user and so the .ssh keys from root could make this work but instead made HA server run under the homeasssistant user).
Next step create a new user on the Pi, gave the user sudo privileges (sudo user mod -aG sudo <username> and copied the keys to the Pi new user
cat ~/.ssh/id_rsa.pub | ssh <USERNAME>@<IP-ADDRESS> 'mkdir -p ~/.ssh && cat >> ~/.ssh/authorized_keys'
next added an entry to the etc/sudoers.d directory for the new user giving access to /usr/local/bin/rfctl, dev/rfctl, and /home/<new user>.
Following this I created a simple shell script to allow running of the command for the switches in position A3 and A4 (I have only 2). The script is given execution privileges
chmod a+x onff4.sh so it can be run using
./onoff4.sh
I can now run the script from the HA command line logged in a the home assistant user like this
ssh -t <newuser>@<piaddress> ./onoff4.sh
OMV – WordPress and NGINX – a further update
I was struggling with WordPress and permalinks. The prior onfiguration I had developed worked fine until I switched to permalinks and then it seems to be picked up the js css etc from the root and not the alias.
Google is wonderful as I found this site – http://www.netz39.de/2014/installation-of-wordpress-in-a-subdirectory-with-nginx/.
I thought it was something to do with the way the try_files was working in relation to fastcgi. It was.
So the wordpress config was update to be as below. Note the location rewrite needs to be at the server level.
location @wordpress_rewrite {
rewrite ^/wordpress/(.*)$ /wordpress/index.php?$1;
}
location /wordpress {
alias /media/13eaa8c9-07ee-4dfc-9d1b-adfae0f0248d/www/wordpress;
add_header Content-Security-Policy "default-src 'self' https: data: 'unsafe-inline' 'unsafe-eval';" always;
add_header X-Content-Type-Options nosniff;
add_header X-XSS-Protection "1; mode=block";
add_header X-Robots-Tag none;
add_header X-Download-Options noopen;
add_header X-Permitted-Cross-Domain-Policies none;
index index.php;
try_files $uri $uri/ @wordpress_rewrite;
location ~* /wordpress/(?:uploads|files)/.*\.php$ {
deny all;
}
location ~ ^/wordpress/(.+\.php)$ {
alias /media/13eaa8c9-07ee-4dfc-9d1b-adfae0f0248d/www/wordpress/$1;
fastcgi_split_path_info ^(.+\.php)(/.*)$;
include fastcgi.conf;
fastcgi_index index.php;
fastcgi_param SCRIPT_FILENAME $request_filename;
fastcgi_pass unix:/var/run/fpm-19e311b1-25e1-4257-8dbc-d49c5ec59015.sock;
}
location = /wordpress/favicon.ico {
access_log off;
log_not_found off;
}
location = /wordpress/robots.txt {
allow all;
access_log off;
log_not_found off;
}
location ~ /wordpress/\. {
deny all;
}
location ~* /wordpress/(?:config)/.*\.php$ {
deny all;
}
location ~* /wordpress/\.(js|css|png|jpg|jpeg|gif|ico)$ {
expires max;
log_not_found off;
}
}
Owntracks and Mosquitto
Came across Owntracks and decided that it would be fun to have my own Mosquitto repository.
Followed instructions here ….
https://www.digitalocean.com/community/questions/how-to-setup-a-mosquitto-mqtt-server-and-receive-data-from-owntracks
They work fine with the exception of needing to install mosquitto-clients to get the mosquitto_sub command working and leaving off the ip address in the mosquitto.conf file from the listener entry. Looking at the log later on the connection is from the ip address of the router on the local lan for external connections and that probably was the address needed to get things working if an ip address was used.
So when I tested and changed the location and config items multiple items are written to the mosquitto database. This then looks bad in the recorder as there are loads of entries which don’t look pretty!
These are in var / spool / owntracks / recorder / store and then either last or rec. If you remove all entries except the ones you want from both then things look pretty again.
It is also worth installing mqtt-spy from mqhive – http://kamilfb.github.io/mqtt-spy/ and publishing a null record without any data or retain so that the mosquitto database does not have then entries any more.
the mosquitto database is normally in var/lib/mosquitto but the location can be changed in the mosquitto.conf or conf.d file in etc/mosquitto.
Now it got tricker when I wanted to publish the steps from my iPhone. Publishing a command did nothing. I found this comment on GitHub …. ”
Remote commands need to be enabled with remoteConfig: export your configuration, add cmd: true, and re-import (e.g. by sending the .otrc file to iOS and open in OwnTracks).
Once you’ve done that, you can send remote commands. Note though, that the iOS app is put to sleep by the OS which means that when it’s in the background you will have to wait until it wakes up for the command to take effect / be processed; this can take a while. Hence we suggest you post commands to iOS with QoS=2″
So I did this and all is well.
mosquitto_pub -q 2 -h xxxx -p 8883 -t owntracks/owntracks/michael-iPhone6s/cmd -u owntracks -P xxx -m ‘{“_type” : “cmd”, “action”: “reportSteps”}’
and this opened the BBC new in the Featured tab. Cool….
mosquitto_pub -q 2 -h xxx -p 8883 -t owntracks/owntracks/michael-iPhone6s/cmd -u owntracks -P xxx -m ‘{“action”: “action”, “url”: “http://news.bbc.co.uk”, “_type”: “cmd”}’
I was a bit puzzled about why the topic was owntracks/owntracks but on further reading of the documentation the default topic is owntracks/username/devicename and as I was using a username of owntracks the second pat of the topic derived from that.
Simple change to remove Nextcloud Allowed Memory exhaused error
I have been trying to get the Nextcloud Gallery working and could not work out why it was just hanging.
What I had not realised is that under “Settings” you can see the log files for Nextcloud and right there are some very useful error messages.
I was getting an Allowed Memory Exhaused Error. A little googling pointed out that perhaps I had not allocated enough memory to PHP to allow it to work.
A quick check of the pool size showed I had allocated 128M. So decided as I have plently of memory to increase the size to 512M and see what happens.
Once NGINX restarted I was able to click on the Gallery and all of the folders appears with the thumbnail files.
So I then rechecked the log file and there we no errors any more.
Fixed.
Updating Next Cloud using the CLI
For some reason I cannot used the included updater. It simply gives a blank screen.
This site really helped. https://blog.netways.de/2017/07/19/how-to-use-nextcloud-cli/
Update / Upgrade
Let’s start with upgrading to the newest version. Go to the directory where your nextcloud is located – there should be a folder called ‘updater’.
[root@nc-vm ~]# cd /var/www/nextcloud/updater
[root@nc-vm ~]
# ls index.php updater.phar
Inside the updater folder is a file called updater.phar.
Now execute the following command.
[root@nc-vm ~]# sudo -u www-data php updater.phar Current version is 11.0.3. Update to Nextcloud 12.0.0 available. (channel: "stable") Following file will be downloaded automatically: https://download.nextcloud.com/server/releases/nextcloud-12.0.0.zip Steps that will be executed: [ ] Check for expected files [ ] Check for write permissions [ ] Enable maintenance mode [ ] Create backup [ ] Downloading [ ] Extracting [ ] Replace entry points [ ] Delete old files [ ] Move new files in place [ ] Done Start update? [y/N] y
Confirm with ‘y’ to start the update.
Info: Pressing Ctrl-C will finish the currently running step and then stops the updater. [] Check for expected files [] Check for write permissions [] Enable maintenance mode [] Create backup [] Downloading [] Extracting [] Replace entry points [] Delete old files [] Move new files in place [] Done Update of code successful. Should the "occ upgrade" command be executed? [Y/n] Y
After the new files have been moved in place you’ll have to confirm to execute the “occ upgrade” command.
Nextcloud or one of the apps require upgrade - only a limited number of commands are available You may use your browser or the occ upgrade command to do the upgrade Set log level to debug Updating database schema Updated database Updating federatedfilesharing ... Updated federatedfilesharing to 1.2.0 Updating files_pdfviewer ... Updated files_pdfviewer to 1.1.1 Updating files_texteditor ... .. .. Checking for update of app workflowengine in appstore Checked for update of app "workflowengine" in appstore Starting code integrity check... Finished code integrity check Update successful Maintenance mode is kept active Reset log level Keep maintenance mode active? [y/N] N
And finally you enter ‘N’ to disable the maintenance mode
Maintenance mode is disabled
And that’s it. But note: even if it tells you that a lot of apps are be updated, you may find that not all of your apps have been updated.
OCC Command
Next we’ll explore the features of the occ command.
[root@nc-vm ~]# cd /var/www/nextcloud
[root@nc-vm ~]
# sudo -u www-data php occ
You will get a long list of the available options and commands.
Nextcloud version 12.0.0
Usage:
command [options] [arguments]
Options:
-h, --help Display this help message
-q, --quiet Do not output any message
-V, --version Display this application version
--ansi Force ANSI output
--no-ansi Disable ANSI output
-n, --no-interaction Do not ask any interactive question
--no-warnings Skip global warnings, show command output only
-v|vv|vvv, --verbose Increase the verbosity of messages: 1 for normal output, 2 for more verbose output and 3 for debug
Available commands:
_completion BASH completion hook.
check check dependencies of the server environment
help Displays help for a command
list Lists commands
status show some status information
..
..
versions
versions:cleanup Delete versions
versions:expire Expires the users file versions
I won’t be able to cover all of them in this post. But I’ll go over a view of them in the following.
Reset Admin Password
This is pretty useful if you forgot your admin password and you find yourself locked out of your Nextcloud.
[root@nc-vm ~]# sudo -u www-data php /var/www/nextcloud/occ user:resetpassword admin Enter a new password: Confirm the new password: Successfully reset password for admin
Change Log Level
Sometimes you to increase the log level to figure out what is wrong. By default the log level is set to ‘warning’ (level 2).
To get more information you’ll have to decrease the number. So 1 is level ‘info’ and 0 is for ‘debug’.
You may also set it to ‘error’ which is level 3 to get less information.
[root@nc-vm ~]# sudo -u www-data php occ log:manage --level 0 Enabled logging backend: file Log level: Debug (0) Log timezone: UTC
Encryption
For server side encryption it’s necessary to enable the encryption app first.
(In Nextcloud Version 12.0.0 and prior enryption does not work with S3 object store as primary storage.)
[root@nc-vm ~]# sudo -u www-data php occ app:enable encryption encryption enabled
And then enable encryption
[root@nc-vm ~]# sudo -u www-data php occ encryption:enable Encryption enabled Default module: OC_DEFAULT_MODULE
Note that only new uploaded files will be encrypted and not the existing ones.
In order to encrypt all existing files of all users you will have to issue the following command:
[root@nc-vm ~]# sudo -u www-data php occ encryption:encrypt-all You are about to encrypt all files stored in your Nextcloud installation. Depending on the number of available files, and their size, this may take quite some time. Please ensure that no user accesses their files during this time! Note: The encryption module you use determines which files get encrypted. Do you really want to continue? (y/n) y
Continue with ‘y’. You may notify the users by mail about their private key passwords.
But this only works if the users have provided their email-addresses.
Encrypt all files with the Default encryption module ==================================================== Create key-pair for every user ------------------------------ This module will encrypt all files in the users files folder initially. Already existing versions and files in the trash bin will not be encrypted. Key-pair created for all users [============================] Start to encrypt users files ---------------------------- all files encrypted [>---------------------------] Generated encryption key passwords ---------------------------------- +-----------+----------------------+ | Username | Private key password | +-----------+----------------------+ | admin | BqaK1WtI | +-----------+----------------------+ A list of all newly created passwords was written to data/oneTimeEncryptionPasswords.csv Each of these users need to login to the web interface, go to the personal settings section "basic encryption module" and update the private key password to match the login password again by entering the one-time password into the "old log-in password" field and their current login password Do you want to send the passwords directly to the users by mail? (y/n) n
Configuration
Usually the config file for Nextcloud is located in /var/www/nextcloud/config.
So in order to change the configuration you may edit the file /var/www/nextcloud/config/config.php with a text editor.
But you can also import a custom config file in json format. In this example I imported a config to set Ceph S3 object store as primary storage for Nextcloud:
[root@nc-vm ~]# cat objectstore.json
{"system": {
"objectstore": {
"class": "OC\\\\Files\\\\ObjectStore\\\\S3",
"arguments": {
"bucket": "$RGW_BUCKET",
"autocreate": true,
"key": "$RGW_KEY",
"secret": "$RGW_SECRET",
"hostname": "$RGW_HOSTNAME",
"use_ssl": true,
"use_path_style": true
}
}
}}
[root@nc-vm ~]
# sudo -u www-data php occ config:import objectstore.json Config successfully imported from: objectstore.json
It’s also possible to view only specific sections of the config:
[root@nc-vm ~]# sudo -u www-data php occ config:system:get objectstore class: OC\\Files\\ObjectStore\\S3 arguments: bucket: $RGW_BUCKET autocreate: true key: $RGW_KEY secret: $RGW_SECRET hostname: $RGW_HOSTNAME use_ssl: true use_path_style: true
Apps
To get a list of all installed enabled and disabled apps:
[root@nc-vm ~]# sudo -u www-data php occ app:list Enabled: - activity: 2.5.2 - bruteforcesettings: 1.0.2 - calendar: 1.5.3 - comments: 1.2.0 .. .. - workflowengine: 1.2.0 Disabled: - admin_audit - encryption - files_external - previewgenerator - user_external - user_ldap
To enable/disable apps:
[root@nc-vm ~]# sudo -u www-data php occ app:enable previewgenerator previewgenerator enabled
[root@nc-vm ~]
# sudo -u www-data php occ app:disable calendar calendar disabled
Like I mentioned before, there are many more commands and the ones I picked are just a view of them.
But I hope they were useful at least for some of you.
OMV – Changes to NGINX for self hosted sites
# server_name openmediavault-webgui;
# change to
server_name my_new_url;
# listen [::]:80 ipv6only=off;
# change to
listen [::]:80 default_server;
# listen [::]:443 ipv6only=off ssl deferred;
# change to
listen [::]:443 default_server;
# include /etc/nginx/openmediavault-webgui.d/*.conf;
# change to
include /etc/nginx/my_new_url_file.d/*.conf;
I then moved all the .conf files and added symlinks back to the opemmediavault files.
Next Cloud – harder as needed to use root and not Alias
location /nextcloud {
root /media/www;
add_header X-Content-Type-Options nosniff;
add_header X-XSS-Protection "1; mode=block";
add_header X-Robots-Tag none;
add_header X-Download-Options noopen;
add_header X-Permitted-Cross-Domain-Policies none;
add_header Strict-Transport-Security "max-age=15768000;includeSubDomains";<br />
location = /nextcloud/robots.txt {
allow all;
access_log off;
log_not_found off;
}
location = /nextcloud/.well-known/carddav {
return 301 $scheme://$host/nextcloud/remote.php/dav;
}
location = /nextcloud/.well-known/caldav {
return 301 $scheme://$host/nextcloud/remote.php/dav;
}
location /nextcloud/.well-known/acme-challenge {
}
rewrite_log on;
# set max upload size
client_max_body_size 512M;
fastcgi_buffers 64 4K;
# Enable gzip but do not remove ETag headers
gzip on;
gzip_vary on;
gzip_comp_level 4;
gzip_min_length 256;
gzip_proxied expired no-cache no-store private no_last_modified no_etag auth;
gzip_types application/atom+xml application/javascript application/json application/ld+json application/manifest+json application/rss+xml application/vnd.geo+json application/vnd.ms-fontobject application/x-font-ttf application/x-web-app-manifest+json application/xhtml+xml application/xml font/opentype image/bmp image/svg+xml image/x-icon text/cache-manifest text/css text/plain text/vcard text/vnd.rim.location.xloc text/vtt text/x-component text/x-cross-domain-policy;
# Uncomment if your server is build with the ngx_pagespeed module
# This module is currently not supported.
#pagespeed off;
location /nextcloud/{
# rewrite ^ /nextcloud/index.php$request_uri;
# rewrite ^/nextcloud/(.*) /nextcloud/$1;
rewrite ^ /nextcloud/index.php$uri;
}
location ~ ^/nextcloud/(?:build|tests|config|lib|3rdparty|templates|data)/ {
deny all;
}
location ~ ^/nextcloud(?:\.|autotest|occ|issue|indie|db_|console) {
deny all;
}
location ~ ^/nextcloud/(?:index|remote|public|cron|core/ajax/update|status|ocs/v[12]|updater/.+|ocs-provider/.+)\.php(?:$|/) {
fastcgi_split_path_info ^(.+?\.php)(/.*)$;
include fastcgi.conf;
fastcgi_param SCRIPT_FILENAME $document_root$fastcgi_script_name;
#fastcgi_param SCRIPT_FILENAME /media/13eaa8c9-07ee-4dfc-9d1b-adfae0f0248d/www/nextcloud/$fastcgi_script_name;
#fastcgi_param SCRIPT_FILENAME $request_filename;
fastcgi_param PATH_INFO $fastcgi_path_info;
fastcgi_param HTTPS on;
#Avoid sending the security headers twice
fastcgi_param modHeadersAvailable true;
fastcgi_param front_controller_active true;
fastcgi_pass unix:/var/run/my_sock_name.sock;
fastcgi_intercept_errors on;
fastcgi_request_buffering off;
}
location ~ ^/(?:updater|ocs-provider)(?:$|/) {
try_files /nextcloud/$uri/ =404;
index index.php;
}
location ~ /nextcloud/(?:$|/)\.(?:js|css|woof|svg|html|ttf|png|jpg|jpeg|gif|ico)$ {
expires max;
log_not_found off;
}
# Adding the cache control header for js and css files
# Make sure it is BELOW the PHP block
location ~ \.(?:css|js|woff|svg|gif)$ {
try_files $uri $uri/ /nextcloud/index.php$request_uri;
add_header Cache-Control "public, max-age=15778463";
# Add headers to serve security related headers (It is intended
# to have those duplicated to the ones above)
# Before enabling Strict-Transport-Security headers please read
# into this topic first.
# add_header Strict-Transport-Security "max-age=15768000;
# includeSubDomains; preload;";
add_header X-Content-Type-Options nosniff;
add_header X-XSS-Protection "1; mode=block";
add_header X-Robots-Tag none;
add_header X-Download-Options noopen;
add_header X-Permitted-Cross-Domain-Policies none;
# Optional: Don't log access to assets
access_log off;
}
location ~ \.(?:png|html|ttf|ico|jpg|jpeg)$ {
try_files $uri $uri/ /nextcloud/index.php$request_uri;
# Optional: Don't log access to other assets
access_log off;
}
}
Firefly
location /firefly {
root /media/www/firefly-iii;
index index.php;
try_files $uri $uri/ /firefly/index.php?$query_string;
autoindex on;
sendfile off;
location ~ \.php$ {
include fastcgi.conf;
fastcgi_index index.php;
fastcgi_param SCRIPT_FILENAME $request_filename;
fastcgi_pass unix:/var/run/my_sock_name.sock;
}
location = /firefly/favicon.ico {
access_log off;
log_not_found off;
}
location = /firefly/robots.txt {
allow all;
access_log off;
log_not_found off;
}
location ~ /firefly/\. {
deny all;
}
location ~* /firefly/(?:config)/.*\.php$ {
deny all;
}
location ~* /firefly/\.(js|css|png|jpg|jpeg|gif|ico)$ {
expires max;
log_not_found off;
}
}
So the fix needed for Webtrees was to have another Server block which was not the same as that here /etc/nginx/sites-available/openmediavault-webgui.
So I copied this file and renamed as a new file matching my site URL.
Added a symlink from /etc/nginx/sites-enabled
Inside the new file I needed to change a few lines …..
# server_name openmediavault-webgui;
# change to
server_name my_new_url;
# listen [::]:80 ipv6only=off;
# change to
listen [::]:80 default_server;
# listen [::]:443 ipv6only=off ssl deferred;
# change to
listen [::]:443 default_server;
# include /etc/nginx/openmediavault-webgui.d/*.conf;
# change to
include /etc/nginx/my_new_url_file.d/*.conf;
I then moved all the .conf files and added symlinks back to the opemmediavault files.
I have wanted to run a number of packages so that all I needed to do was to type in the IP address of the OMV/package_name. I also wanted to run these from a separate drive in my case mapped to /media/www/package_name.
I struggled with the NGINX configuration but there were clues in the way Mysql is implemented in the NGINX .conf files. I thought I would share what I did and if someone can improve on this great.
Firstly worth saying I have Webmin installed which helps with the configuration and I have included the NGINX plugin for Webmin.
OMV stores the config in /etc/nginx/sites-available/openmediavault-webgui. (note NGINX only uses these configurations if there is a symlink from the /etc/nginx/sites-enabled folder.
If you examine this folder it has at the bottom a line which is
include /etc/nginx/openmediavault-webgui.d/*.conf;
So this indicates we can include additional configurations in the folder /etc/nginx/openmediavault-webgui.d. And sure enough there is one for Mysql – openmediavault-mysql-management-site.conf.
The PHP sock is in this line
fastcgi_pass unix:/var/run/php-fpm-openmediavault-mysql.sock. And you can see the shortcut to the file if you take a look in /var/run. The actual PHP config are held in /etc/php/7.0/fpm/pool.d.
This is important as I did not want to change the openmediavault-webgui.d so any future changes to OMV would not overwrite my changes.
These pool.d files are written using the NGINX plugin in OMV. So if you add a Pool via the NGINX plugin it creates the pool.d folder file after first writing the config to the /etc/openmediavault/config.xml. See more about this here openmediavault.readthedocs.io/…opment/internaltools.html
So I figured that I could use the NGINX plugin to create the pool.d files and the associated symlink in /var/run and create my own nginx .conf files in /etc/nginx/openmediavault-webgui.d folder by copying the openmediavault-mysql-management-site.conf and altering the link to the .sock file. i.e. changing the line fastcgi_pass unix:/var/run/php-fpm-openmediavault-mysql.sock. to fastcgi_pass unix:/var/run/my_new_nginx_name.sock in the copied file.
I successfully added
1. WordPress
2. Nextcloud
3. Piwigo
4. Firefly
5. Webtrees
6. Extplorer
The config was slightly different for each one and Webtrees was particularly tricky for me and the URL was changed to have the server “openmediavault-webgui” in the file /etc/nginx/sites-available/openmediavault-webgui replacing the url after openmediavault-webgui/webtrees which messed by everything. More on Webtrees lower in the post.
So for WordPress the NGINX .conf file is (similar for Piwigo and Extplorer and Webtrees)
location /wordpress {
alias /media/13eaa8c9-07ee-4dfc-9d1b-adfae0f0248d/www/wordpress;
add_header Content-Security-Policy "default-src 'self' https: data: 'unsafe-inline' 'unsafe-eval';" always;
index index.php;
try_files $uri $uri/ index.php;
location ~ \.php$ {
include fastcgi.conf;
fastcgi_index index.php;
fastcgi_param SCRIPT_FILENAME $request_filename;
fastcgi_pass unix:/var/run/fpm-19e311b1-25e1-4257-8dbc-d49c5ec59015.sock;
#fastcgi_pass unix:/var/run/php5-fpm.sock;
}
location = /wordpress/favicon.ico {
access_log off;
log_not_found off;
}
location = /wordpress/robots.txt {
allow all;
access_log off;
log_not_found off;
}
location ~ /wordpress/\. {
deny all;
}
location ~* /wordpress/(?:config)/.*\.php$ {
deny all;
}
location ~* /wordpress/\.(js|css|png|jpg|jpeg|gif|ico)$ {
expires max;
log_not_found off;
}
}
Next Cloud – harder as needed to use root and not Alias
location /nextcloud {
root /media/www;
add_header X-Content-Type-Options nosniff;
add_header X-XSS-Protection "1; mode=block";
add_header X-Robots-Tag none;
add_header X-Download-Options noopen;
add_header X-Permitted-Cross-Domain-Policies none;
add_header Strict-Transport-Security "max-age=15768000;includeSubDomains";<br />
location = /nextcloud/robots.txt {
allow all;
access_log off;
log_not_found off;
}
location = /nextcloud/.well-known/carddav {
return 301 $scheme://$host/nextcloud/remote.php/dav;
}
location = /nextcloud/.well-known/caldav {
return 301 $scheme://$host/nextcloud/remote.php/dav;
}
location /nextcloud/.well-known/acme-challenge {
}
rewrite_log on;
# set max upload size
client_max_body_size 512M;
fastcgi_buffers 64 4K;
# Enable gzip but do not remove ETag headers
gzip on;
gzip_vary on;
gzip_comp_level 4;
gzip_min_length 256;
gzip_proxied expired no-cache no-store private no_last_modified no_etag auth;
gzip_types application/atom+xml application/javascript application/json application/ld+json application/manifest+json application/rss+xml application/vnd.geo+json application/vnd.ms-fontobject application/x-font-ttf application/x-web-app-manifest+json application/xhtml+xml application/xml font/opentype image/bmp image/svg+xml image/x-icon text/cache-manifest text/css text/plain text/vcard text/vnd.rim.location.xloc text/vtt text/x-component text/x-cross-domain-policy;
# Uncomment if your server is build with the ngx_pagespeed module
# This module is currently not supported.
#pagespeed off;
location /nextcloud/{
# rewrite ^ /nextcloud/index.php$request_uri;
# rewrite ^/nextcloud/(.*) /nextcloud/$1;
rewrite ^ /nextcloud/index.php$uri;
}
location ~ ^/nextcloud/(?:build|tests|config|lib|3rdparty|templates|data)/ {
deny all;
}
location ~ ^/nextcloud(?:\.|autotest|occ|issue|indie|db_|console) {
deny all;
}
location ~ ^/nextcloud/(?:index|remote|public|cron|core/ajax/update|status|ocs/v[12]|updater/.+|ocs-provider/.+)\.php(?:$|/) {
fastcgi_split_path_info ^(.+?\.php)(/.*)$;
include fastcgi.conf;
fastcgi_param SCRIPT_FILENAME $document_root$fastcgi_script_name;
#fastcgi_param SCRIPT_FILENAME /media/13eaa8c9-07ee-4dfc-9d1b-adfae0f0248d/www/nextcloud/$fastcgi_script_name;
#fastcgi_param SCRIPT_FILENAME $request_filename;
fastcgi_param PATH_INFO $fastcgi_path_info;
fastcgi_param HTTPS on;
#Avoid sending the security headers twice
fastcgi_param modHeadersAvailable true;
fastcgi_param front_controller_active true;
fastcgi_pass unix:/var/run/my_sock_name.sock;
fastcgi_intercept_errors on;
fastcgi_request_buffering off;
}
location ~ ^/(?:updater|ocs-provider)(?:$|/) {
try_files /nextcloud/$uri/ =404;
index index.php;
}
location ~ /nextcloud/(?:$|/)\.(?:js|css|woof|svg|html|ttf|png|jpg|jpeg|gif|ico)$ {
expires max;
log_not_found off;
}
# Adding the cache control header for js and css files
# Make sure it is BELOW the PHP block
location ~ \.(?:css|js|woff|svg|gif)$ {
try_files $uri $uri/ /nextcloud/index.php$request_uri;
add_header Cache-Control "public, max-age=15778463";
# Add headers to serve security related headers (It is intended
# to have those duplicated to the ones above)
# Before enabling Strict-Transport-Security headers please read
# into this topic first.
# add_header Strict-Transport-Security "max-age=15768000;
# includeSubDomains; preload;";
add_header X-Content-Type-Options nosniff;
add_header X-XSS-Protection "1; mode=block";
add_header X-Robots-Tag none;
add_header X-Download-Options noopen;
add_header X-Permitted-Cross-Domain-Policies none;
# Optional: Don't log access to assets
access_log off;
}
location ~ \.(?:png|html|ttf|ico|jpg|jpeg)$ {
try_files $uri $uri/ /nextcloud/index.php$request_uri;
# Optional: Don't log access to other assets
access_log off;
}
}
Firefly
location /firefly {
root /media/www/firefly-iii;
index index.php;
try_files $uri $uri/ /firefly/index.php?$query_string;
autoindex on;
sendfile off;
location ~ \.php$ {
include fastcgi.conf;
fastcgi_index index.php;
fastcgi_param SCRIPT_FILENAME $request_filename;
fastcgi_pass unix:/var/run/my_sock_name.sock;
}
location = /firefly/favicon.ico {
access_log off;
log_not_found off;
}
location = /firefly/robots.txt {
allow all;
access_log off;
log_not_found off;
}
location ~ /firefly/\. {
deny all;
}
location ~* /firefly/(?:config)/.*\.php$ {
deny all;
}
location ~* /firefly/\.(js|css|png|jpg|jpeg|gif|ico)$ {
expires max;
log_not_found off;
}
}
So the fix needed for Webtrees was to have another Server block which was not the same as that here /etc/nginx/sites-available/openmediavault-webgui.
So I copied this file and renamed as a new file matching my site URL.
Added a symlink from /etc/nginx/sites-enabled
Inside the new file I needed to change a few lines …..
# server_name openmediavault-webgui;
# change to
server_name my_new_url;
# listen [::]:80 ipv6only=off;
# change to
listen [::]:80 default_server;
# listen [::]:443 ipv6only=off ssl deferred;
# change to
listen [::]:443 default_server;
# include /etc/nginx/openmediavault-webgui.d/*.conf;
# change to
include /etc/nginx/my_new_url_file.d/*.conf;
I then moved all the .conf files and added symlinks back to the opemmediavault files.
I have wanted to run a number of packages so that all I needed to do was to type in the IP address of the OMV/package_name. I also wanted to run these from a separate drive in my case mapped to /media/www/package_name.
I struggled with the NGINX configuration but there were clues in the way Mysql is implemented in the NGINX .conf files. I thought I would share what I did and if someone can improve on this great.
Firstly worth saying I have Webmin installed which helps with the configuration and I have included the NGINX plugin for Webmin.
OMV stores the config in /etc/nginx/sites-available/openmediavault-webgui. (note NGINX only uses these configurations if there is a symlink from the /etc/nginx/sites-enabled folder.
If you examine this folder it has at the bottom a line which is
include /etc/nginx/openmediavault-webgui.d/*.conf;
So this indicates we can include additional configurations in the folder /etc/nginx/openmediavault-webgui.d. And sure enough there is one for Mysql – openmediavault-mysql-management-site.conf.
The PHP sock is in this line
fastcgi_pass unix:/var/run/php-fpm-openmediavault-mysql.sock. And you can see the shortcut to the file if you take a look in /var/run. The actual PHP config are held in /etc/php/7.0/fpm/pool.d.
This is important as I did not want to change the openmediavault-webgui.d so any future changes to OMV would not overwrite my changes.
These pool.d files are written using the NGINX plugin in OMV. So if you add a Pool via the NGINX plugin it creates the pool.d folder file after first writing the config to the /etc/openmediavault/config.xml. See more about this here openmediavault.readthedocs.io/…opment/internaltools.html
So I figured that I could use the NGINX plugin to create the pool.d files and the associated symlink in /var/run and create my own nginx .conf files in /etc/nginx/openmediavault-webgui.d folder by copying the openmediavault-mysql-management-site.conf and altering the link to the .sock file. i.e. changing the line fastcgi_pass unix:/var/run/php-fpm-openmediavault-mysql.sock. to fastcgi_pass unix:/var/run/my_new_nginx_name.sock in the copied file.
I successfully added
1. WordPress
2. Nextcloud
3. Piwigo
4. Firefly
5. Webtrees
6. Extplorer
The config was slightly different for each one and Webtrees was particularly tricky for me and the URL was changed to have the server “openmediavault-webgui” in the file /etc/nginx/sites-available/openmediavault-webgui replacing the url after openmediavault-webgui/webtrees which messed by everything. More on Webtrees lower in the post.
So for WordPress the NGINX .conf file is (similar for Piwigo and Extplorer and Webtrees)
location /wordpress {
alias /media/13eaa8c9-07ee-4dfc-9d1b-adfae0f0248d/www/wordpress;
add_header Content-Security-Policy "default-src 'self' https: data: 'unsafe-inline' 'unsafe-eval';" always;
index index.php;
try_files $uri $uri/ index.php;
location ~ \.php$ {
include fastcgi.conf;
fastcgi_index index.php;
fastcgi_param SCRIPT_FILENAME $request_filename;
fastcgi_pass unix:/var/run/fpm-19e311b1-25e1-4257-8dbc-d49c5ec59015.sock;
#fastcgi_pass unix:/var/run/php5-fpm.sock;
}
location = /wordpress/favicon.ico {
access_log off;
log_not_found off;
}
location = /wordpress/robots.txt {
allow all;
access_log off;
log_not_found off;
}
location ~ /wordpress/\. {
deny all;
}
location ~* /wordpress/(?:config)/.*\.php$ {
deny all;
}
location ~* /wordpress/\.(js|css|png|jpg|jpeg|gif|ico)$ {
expires max;
log_not_found off;
}
}
Next Cloud – harder as needed to use root and not Alias
location /nextcloud {
root /media/www;
add_header X-Content-Type-Options nosniff;
add_header X-XSS-Protection "1; mode=block";
add_header X-Robots-Tag none;
add_header X-Download-Options noopen;
add_header X-Permitted-Cross-Domain-Policies none;
add_header Strict-Transport-Security "max-age=15768000;includeSubDomains";<br />
location = /nextcloud/robots.txt {
allow all;
access_log off;
log_not_found off;
}
location = /nextcloud/.well-known/carddav {
return 301 $scheme://$host/nextcloud/remote.php/dav;
}
location = /nextcloud/.well-known/caldav {
return 301 $scheme://$host/nextcloud/remote.php/dav;
}
location /nextcloud/.well-known/acme-challenge {
}
rewrite_log on;
# set max upload size
client_max_body_size 512M;
fastcgi_buffers 64 4K;
# Enable gzip but do not remove ETag headers
gzip on;
gzip_vary on;
gzip_comp_level 4;
gzip_min_length 256;
gzip_proxied expired no-cache no-store private no_last_modified no_etag auth;
gzip_types application/atom+xml application/javascript application/json application/ld+json application/manifest+json application/rss+xml application/vnd.geo+json application/vnd.ms-fontobject application/x-font-ttf application/x-web-app-manifest+json application/xhtml+xml application/xml font/opentype image/bmp image/svg+xml image/x-icon text/cache-manifest text/css text/plain text/vcard text/vnd.rim.location.xloc text/vtt text/x-component text/x-cross-domain-policy;
# Uncomment if your server is build with the ngx_pagespeed module
# This module is currently not supported.
#pagespeed off;
location /nextcloud/{
# rewrite ^ /nextcloud/index.php$request_uri;
# rewrite ^/nextcloud/(.*) /nextcloud/$1;
rewrite ^ /nextcloud/index.php$uri;
}
location ~ ^/nextcloud/(?:build|tests|config|lib|3rdparty|templates|data)/ {
deny all;
}
location ~ ^/nextcloud(?:\.|autotest|occ|issue|indie|db_|console) {
deny all;
}
location ~ ^/nextcloud/(?:index|remote|public|cron|core/ajax/update|status|ocs/v[12]|updater/.+|ocs-provider/.+)\.php(?:$|/) {
fastcgi_split_path_info ^(.+?\.php)(/.*)$;
include fastcgi.conf;
fastcgi_param SCRIPT_FILENAME $document_root$fastcgi_script_name;
#fastcgi_param SCRIPT_FILENAME /media/13eaa8c9-07ee-4dfc-9d1b-adfae0f0248d/www/nextcloud/$fastcgi_script_name;
#fastcgi_param SCRIPT_FILENAME $request_filename;
fastcgi_param PATH_INFO $fastcgi_path_info;
fastcgi_param HTTPS on;
#Avoid sending the security headers twice
fastcgi_param modHeadersAvailable true;
fastcgi_param front_controller_active true;
fastcgi_pass unix:/var/run/my_sock_name.sock;
fastcgi_intercept_errors on;
fastcgi_request_buffering off;
}
location ~ ^/(?:updater|ocs-provider)(?:$|/) {
try_files /nextcloud/$uri/ =404;
index index.php;
}
location ~ /nextcloud/(?:$|/)\.(?:js|css|woof|svg|html|ttf|png|jpg|jpeg|gif|ico)$ {
expires max;
log_not_found off;
}
# Adding the cache control header for js and css files
# Make sure it is BELOW the PHP block
location ~ \.(?:css|js|woff|svg|gif)$ {
try_files $uri $uri/ /nextcloud/index.php$request_uri;
add_header Cache-Control "public, max-age=15778463";
# Add headers to serve security related headers (It is intended
# to have those duplicated to the ones above)
# Before enabling Strict-Transport-Security headers please read
# into this topic first.
# add_header Strict-Transport-Security "max-age=15768000;
# includeSubDomains; preload;";
add_header X-Content-Type-Options nosniff;
add_header X-XSS-Protection "1; mode=block";
add_header X-Robots-Tag none;
add_header X-Download-Options noopen;
add_header X-Permitted-Cross-Domain-Policies none;
# Optional: Don't log access to assets
access_log off;
}
location ~ \.(?:png|html|ttf|ico|jpg|jpeg)$ {
try_files $uri $uri/ /nextcloud/index.php$request_uri;
# Optional: Don't log access to other assets
access_log off;
}
}
Firefly
location /firefly {
root /media/www/firefly-iii;
index index.php;
try_files $uri $uri/ /firefly/index.php?$query_string;
autoindex on;
sendfile off;
location ~ \.php$ {
include fastcgi.conf;
fastcgi_index index.php;
fastcgi_param SCRIPT_FILENAME $request_filename;
fastcgi_pass unix:/var/run/my_sock_name.sock;
}
location = /firefly/favicon.ico {
access_log off;
log_not_found off;
}
location = /firefly/robots.txt {
allow all;
access_log off;
log_not_found off;
}
location ~ /firefly/\. {
deny all;
}
location ~* /firefly/(?:config)/.*\.php$ {
deny all;
}
location ~* /firefly/\.(js|css|png|jpg|jpeg|gif|ico)$ {
expires max;
log_not_found off;
}
}
So the fix needed for Webtrees was to have another Server block which was not the same as that here /etc/nginx/sites-available/openmediavault-webgui.
So I copied this file and renamed as a new file matching my site URL.
Added a symlink from /etc/nginx/sites-enabled
Inside the new file I needed to change a few lines …..
# server_name openmediavault-webgui;
# change to
server_name my_new_url;
# listen [::]:80 ipv6only=off;
# change to
listen [::]:80 default_server;
# listen [::]:443 ipv6only=off ssl deferred;
# change to
listen [::]:443 default_server;
# include /etc/nginx/openmediavault-webgui.d/*.conf;
# change to
include /etc/nginx/my_new_url_file.d/*.conf;
I then moved all the .conf files and added symlinks back to the opemmediavault files. Firefly III on OMV
Once Composer was installed started to follow instructions on the Firefly site —>
https://firefly-iii.readthedocs.io/en/latest/installation/server.html
and also here
https://gist.github.com/philthynz/ec04833a8e39c7f7d1b0d33cb4197a95
In order to have Firefly running without access to other users I created a new user for Firefly.
A new SQL database was added using mysql with the new users being the users allowed the complete access to the new database.
When I first ran the install command
composer create-project grumpydictator/firefly-iii --no-dev --prefer-dist firefly-iii 4.7.5
I got the following error
[InvalidArgumentException] Could not find package grumpydictator/firefly-iii with version 4.7.5 in a version installable using your PHP version 7.0.30.
Following this through by looking at the available packages at https://packagist.org/packages/grumpydictator/firefly-iii highlighted that version 4.7.5 needed PHP 7.1. This is not yet available on Debian as an official release. Further searching at the packagist site shows that the latest version for PHP 7.0 is 4.6.3.1. I installed this and all was OK.
But I want the latest release. So I googled and found there is a 7.2 release. See here https://www.chris-shaw.com/blog/installing-php-7.2-on-debian-8-jessie-and-debian-9-stretch. I installed this following the instructions. A few extra packages were needed to get all OK for Firefly php7.2-zip, php7.2-bcmath, php7.2-intl.
It is worth noting that the installer creates the directory for Firefly and you do not need to create this first. If the installer fails however the directory the installer creates needs to be deleted before the installer is run again.
This time I ran
composer create-project grumpydictator/firefly-iii --no-dev --prefer-dist firefly-iii 4.7.5.3
and it worked fine
Installing grumpydictator/firefly-iii (4.7.5.3)
- Installing grumpydictator/firefly-iii (4.7.5.3): Loading from cache
Created project in firefly-iii
&amp;amp;amp;amp;amp;amp;amp;amp;amp;amp;amp;amp;amp;amp;gt; @php -r "file_exists('.env') || copy('.env.example', '.env');"
&amp;amp;amp;amp;amp;amp;amp;amp;amp;amp;amp;amp;amp;amp;gt; @php -r "if (!(getenv('DYNO'))===false){file_exists('.env') || copy('.env.heroku', '.env');}"
Loading composer repositories with package information
Installing dependencies from lock file
Package operations: 62 installs, 0 updates, 0 removals
- Installing bacon/bacon-qr-code (1.0.3): Downloading (100%)
- Installing psr/http-message (1.0.1): Downloading (100%)
- Installing guzzlehttp/psr7 (1.4.2): Downloading (100%)
- Installing guzzlehttp/promises (v1.3.1): Downloading (100%)
- Installing guzzlehttp/guzzle (6.3.3): Downloading (100%)
- Installing bunq/sdk_php (dev-master 8c1faef): Downloading (100%)
- Installing vlucas/phpdotenv (v2.5.0): Downloading (100%)
- Installing symfony/css-selector (v4.1.2): Downloading (100%)
- Installing tijsverkoyen/css-to-inline-styles (2.2.1): Downloading (100%)
- Installing symfony/polyfill-php72 (v1.8.0): Downloading (100%)
- Installing symfony/polyfill-mbstring (v1.8.0): Downloading (100%)
- Installing symfony/var-dumper (v4.1.2): Downloading (100%)
- Installing symfony/routing (v4.1.2): Downloading (100%)
- Installing symfony/process (v4.1.2): Downloading (100%)
- Installing symfony/polyfill-ctype (v1.8.0): Downloading (100%)
- Installing symfony/http-foundation (v4.1.2): Downloading (100%)
- Installing symfony/event-dispatcher (v4.1.2): Downloading (100%)
- Installing psr/log (1.0.2): Loading from cache
- Installing symfony/debug (v4.1.2): Downloading (100%)
- Installing symfony/http-kernel (v4.1.2): Downloading (100%)
- Installing symfony/finder (v4.1.2): Downloading (100%)
- Installing symfony/console (v4.1.2): Downloading (100%)
- Installing doctrine/lexer (v1.0.1): Loading from cache
- Installing egulias/email-validator (2.1.4): Downloading (100%)
- Installing swiftmailer/swiftmailer (v6.1.2): Downloading (100%)
- Installing paragonie/random_compat (v2.0.17): Downloading (100%)
- Installing ramsey/uuid (3.8.0): Downloading (100%)
- Installing psr/simple-cache (1.0.1): Downloading (100%)
- Installing psr/container (1.0.0): Downloading (100%)
- Installing symfony/translation (v4.1.2): Downloading (100%)
- Installing nesbot/carbon (1.25.0): Downloading (100%)
- Installing monolog/monolog (1.23.0): Loading from cache
- Installing league/flysystem (1.0.45): Downloading (100%)
- Installing erusev/parsedown (1.7.1): Downloading (100%)
- Installing dragonmantank/cron-expression (v2.2.0): Downloading (100%)
- Installing doctrine/inflector (v1.3.0): Downloading (100%)
- Installing laravel/framework (v5.6.29): Downloading (100%)
- Installing davejamesmiller/laravel-breadcrumbs (5.1.0): Downloading (100%)
- Installing doctrine/event-manager (v1.0.0): Downloading (100%)
- Installing doctrine/cache (v1.7.1): Downloading (100%)
- Installing doctrine/dbal (v2.8.0): Downloading (100%)
- Installing fideloper/proxy (4.0.0): Downloading (100%)
- Installing zendframework/zend-diactoros (1.8.3): Downloading (100%)
- Installing symfony/psr-http-message-bridge (v1.0.2): Downloading (100%)
- Installing phpseclib/phpseclib (2.0.11): Downloading (100%)
- Installing league/event (2.1.2): Downloading (100%)
- Installing lcobucci/jwt (3.2.2): Downloading (100%)
- Installing defuse/php-encryption (v2.2.1): Downloading (100%)
- Installing league/oauth2-server (6.1.1): Downloading (100%)
- Installing firebase/php-jwt (v5.0.0): Downloading (100%)
- Installing laravel/passport (v5.0.3): Downloading (100%)
- Installing laravelcollective/html (v5.6.10): Downloading (100%)
- Installing league/commonmark (0.17.5): Downloading (100%)
- Installing league/csv (9.1.4): Downloading (100%)
- Installing league/fractal (0.17.0): Downloading (100%)
- Installing paragonie/constant_time_encoding (v2.2.2): Downloading (100%)
- Installing symfony/polyfill-util (v1.8.0): Downloading (100%)
- Installing symfony/polyfill-php56 (v1.8.0): Downloading (100%)
- Installing pragmarx/google2fa (v3.0.1): Downloading (100%)
- Installing pragmarx/google2fa-laravel (v0.2.0): Downloading (100%)
- Installing twig/twig (v1.35.4): Downloading (100%)
- Installing rcrowe/twigbridge (v0.9.6): Downloading (100%)
Generating optimized autoload files
&amp;amp;amp;amp;amp;amp;amp;amp;amp;amp;amp;amp;amp;amp;gt; Illuminate\Foundation\ComposerScripts::postAutoloadDump
&amp;amp;amp;amp;amp;amp;amp;amp;amp;amp;amp;amp;amp;amp;gt; php artisan firefly:instructions install
+------------------------------------------------------------------------------+
| |
| Thank you for installing Firefly III, v4.7.5.3! |
| |
| |
+------------------------------------------------------------------------------+
&amp;amp;amp;amp;amp;amp;amp;amp;amp;amp;amp;amp;amp;amp;gt; @php artisan key:generate
and the key needed for config is generated.
So artisan is part of PHP 7.2 and not PHP 7.0!
I have not listed the key for obvious reasons!!
The .env file was then updated following the instructions here https://gist.github.com/philthynz/ec04833a8e39c7f7d1b0d33cb4197a95
and then the following command run
/media/www/firefly-iii# php artisan migrate:refresh --seed
with this result
Migration table not found. Migration table created successfully. Migrating: 2016_06_16_000000_create_support_tables Migrated: 2016_06_16_000000_create_support_tables Migrating: 2016_06_16_000001_create_users_table Migrated: 2016_06_16_000001_create_users_table Migrating: 2016_06_16_000002_create_main_tables Migrated: 2016_06_16_000002_create_main_tables Migrating: 2016_08_25_091522_changes_for_3101 Migrated: 2016_08_25_091522_changes_for_3101 Migrating: 2016_09_12_121359_fix_nullables Migrated: 2016_09_12_121359_fix_nullables Migrating: 2016_10_09_150037_expand_transactions_table Migrated: 2016_10_09_150037_expand_transactions_table Migrating: 2016_10_22_075804_changes_for_v410 Migrated: 2016_10_22_075804_changes_for_v410 Migrating: 2016_11_24_210552_changes_for_v420 Migrated: 2016_11_24_210552_changes_for_v420 Migrating: 2016_12_22_150431_changes_for_v430 Migrated: 2016_12_22_150431_changes_for_v430 Migrating: 2016_12_28_203205_changes_for_v431 Migrated: 2016_12_28_203205_changes_for_v431 Migrating: 2017_04_13_163623_changes_for_v440 Migrated: 2017_04_13_163623_changes_for_v440 Migrating: 2017_06_02_105232_changes_for_v450 Migrated: 2017_06_02_105232_changes_for_v450 Migrating: 2017_08_20_062014_changes_for_v470 Migrated: 2017_08_20_062014_changes_for_v470 Migrating: 2017_11_04_170844_changes_for_v470a Migrated: 2017_11_04_170844_changes_for_v470a Migrating: 2018_01_01_000001_create_oauth_auth_codes_table Migrated: 2018_01_01_000001_create_oauth_auth_codes_table Migrating: 2018_01_01_000002_create_oauth_access_tokens_table Migrated: 2018_01_01_000002_create_oauth_access_tokens_table Migrating: 2018_01_01_000003_create_oauth_refresh_tokens_table Migrated: 2018_01_01_000003_create_oauth_refresh_tokens_table Migrating: 2018_01_01_000004_create_oauth_clients_table Migrated: 2018_01_01_000004_create_oauth_clients_table Migrating: 2018_01_01_000005_create_oauth_personal_access_clients_table Migrated: 2018_01_01_000005_create_oauth_personal_access_clients_table Migrating: 2018_03_19_141348_changes_for_v472 Migrated: 2018_03_19_141348_changes_for_v472 Migrating: 2018_04_07_210913_changes_for_v473 Migrated: 2018_04_07_210913_changes_for_v473 Migrating: 2018_04_29_174524_changes_for_v474 Migrated: 2018_04_29_174524_changes_for_v474 Migrating: 2018_06_08_200526_changes_for_v475 Migrated: 2018_06_08_200526_changes_for_v475 Seeding: AccountTypeSeeder Seeding: TransactionCurrencySeeder Seeding: TransactionTypeSeeder Seeding: PermissionSeeder Seeding: LinkTypeSeeder Seeding: ConfigSeeder
and then this run
/media/www/firefly-iii# php artisan passport:install Encryption keys generated successfully. Personal access client created successfully. Client ID: 1 Client Secret: .......... Password grant client created successfully. Client ID: 2 Client Secret: ........
Continue to follow instructions
Update Postfix
Update Aliases
Change ownership of directory firefly-iii to www-data for NGINX and PHP
From this point I changed direction and decided to use the NGINX plug in for OMV and add a sock for Firefly.
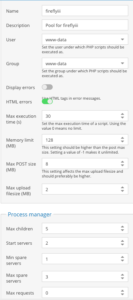
And the could never get to work. The tried to address a php7.2 error and ended up by mistake deleting OMV again!
So started again. I am deciding to run this only with supported packages. i.e. I’ll wait for PHP 7+ on Debian.
So basically did the steps above again. Created a new sock.
The NGINX configuration was a bit tricky but this worked in the end.
location /firefly {
root /path to install/firefly-iii;
index index.php;
try_files $uri $uri/ /firefly/index.php?$query_string;
autoindex on;
sendfile off;
location ~ \.php$ {
include fastcgi.conf;
fastcgi_index index.php;
fastcgi_param SCRIPT_FILENAME $request_filename;
fastcgi_pass unix:/var/run/sockname.sock;
}
location = /firefly/favicon.ico {
access_log off;
log_not_found off;
}
location = /firefly/robots.txt {
allow all;
access_log off;
log_not_found off;
}
location ~ /firefly/\. {
deny all;
}
location ~* /firefly/(?:config)/.*\.php$ {
deny all;
}
location ~* /firefly/\.(js|css|png|jpg|jpeg|gif|ico)$ {
expires max;
log_not_found off;
}
}
Recursive changes for CHMOD and CHOWN
So more trouble with the OMV box and associated link to the Synology Diskstation! Another story.
However I have moved the Family History site based on Webtrees to the OMV having mistakenly deleted every file in the /volume1/web directory. Luckly it changes very seldomly and I had an sql backup which was OK.
However the install does not seem to give the right directory or file permissions. I have done a CHOWN to give www-data as both user and group but now want to recursively have directories as 755 an files as 644.
find /media/www/webtrees -type d -exec chmod 755 {} \;
and
find /media/www/webtrees -type f -exec chmod 644 {} \;
does the trick.
